Содержание
Short summary
At the end of April 2021, Digital Observers (volunteer community) recorded anomalies in the processing of DNS queries in the networks of Belarusian providers connected to the global Internet through the NTEC* (National Traffic Exchange Center) network. The state infrastructure provider spoofs the DNS response for the resources: belarus2020.org, golos2020.org, golos-belarus2020.org, tempail.com. When navigating to these sites, the user does not receive a response and the connection is interrupted. Spoofing occurs even if the user accesses public DNS servers, for example 8.8.8.8.
In our opinion, this is a variant of “blocking” sites from the restricted access list, not provided for by the current legislation, and extremely dangerous for all Internet users from Belarus. Based on the experience of Turkey, Syria and Egypt, where the authorities also used this method, it can be assumed that this could lead to the Internet on “white lists”, substitution of content and entire sites, and deliberate mass infection of user devices with spyware and similar severity of consequences
Currently in Belarus there are practically no opportunities to challenge this practice in the legal field. There is a need for widespread education of users about the emergence of such practices and the possible consequences. On an individual level, users can secure themselves with a VPN. Providers also have tools to protect their users.
Full version
*The National Traffic Exchange Center is one of the two monopoly providers in Belarus, from which all other providers buy traffic to go abroad.
What is DNS?
DNS – Domain Name System. This is a kind of “phone book” in which human-readable addresses such as www.microsoft.com are converted into IP addresses. There are many DNS servers, and usually they are located at providers so that the user does not wait for a server response for too long, but opens the site as quickly as possible. Provider’s DNS servers store the results of responses in a cache and respond to new requests faster.
How does a URL work?
DNS servers are offered by the provider, but the user can register alternative DNS servers manually, for example, by specifying the address 8.8.8.8. – Google DNS server or any other.
When a user types a site address (URL), for example, google.com, his device turns to such a DNS server in order to receive the IP address of this site in response. After receiving such a DNS response, a transition is made to the specified address. If the server does not have a response in the cache, then it contacts another, higher-level DNS server and receives a response from it.
It is important to mention that DNS communication is unencrypted. That is, all providers along the path of the request “see” which DNS servers the user is addressing, which requests are sent and what they are responding to.
What happened?
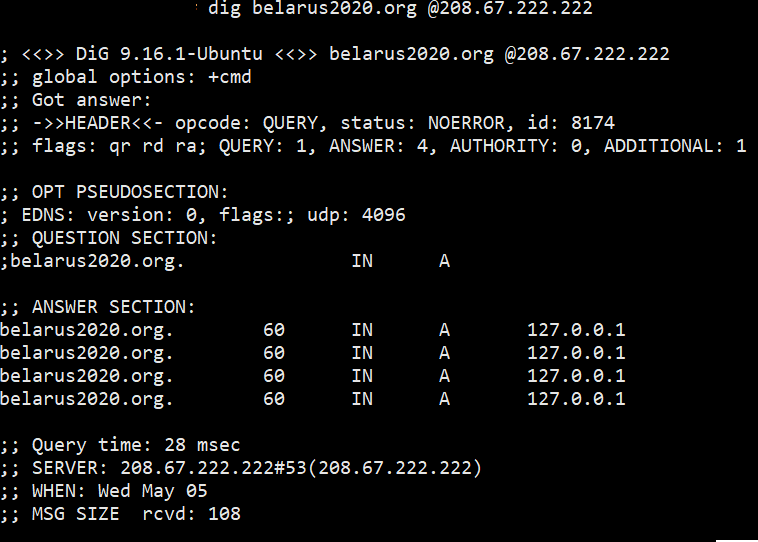
We found that users whose providers go abroad through the state provider NTEC (National Traffic Exchange Center), which itself does not provide traffic to end users, but sells it to other providers (Business Network, A1, MTS, CosmosTV and many others), spoofs the DNS response for the resources: belarus2020.org, golos2020.org, golos-belarus2020.org, tempail.com and gives the address 127.0.0.1 as a response. By default, this is always the IP address of the computer from which the request originates.
* For the resource protonmail.com, the spoofing took place at the time of measurements on April 15, as of May 4, there is no spoofing for this domain.
This means that when clicking on the given URL, the user does not receive a response and the connection is interrupted, and the user sees that the site is unavailable.
Moreover, even if a user accesses public DNS servers, for example, 8.8.8.8, since this passes through open channels, at the NTEC level, some technology intercepts this request and sends a DNS response with the address 127.0.0.1 as a response. We checked this on several popular DNS servers (9.9.9.9 – Quad9, 208.67.222.222 – OpenDNS, 8.26.56.26 – Comodo Secure DNS) and for 4 specified domains received the same response, spoofed content.
In our opinion, this is a variant of the implementation of “blocking” sites from the restricted access list.
What is the problem?
DNS spoofing is considered a variant of the MiTM attack. This is when cybercriminals interfere with the unprotected part of the traffic in order to cause any harm, in this case – to show the user not the site to which he accessed, but some other, for example, phishing. The implementation of this technology at the provider level undermines the trust in the provider, because in this way the NTEC can fake a DNS request for absolutely any site and an ordinary user will not notice anything. At the same time, NTEC makes a spoofing for DNS queries for all providers who buy traffic from it.
A similar thing has already happened in Belarus, when on August 9 the site of “Golos” was changed – then users who went to the address of “Golos” via http saw a fake site that offered to enter their phone number.
Similar attacks have already happened in other countries. For example, in Turkey, the attackers changed the links on the official sites of utilities for Windows: CCleaner, Avast Antivirus, 7-zip, Opera. The attack looked like this: the user went to the official website via https and clicked on the “download” button, which led to the http-address. When the user’s device sent a DNS request, then using DPI technology, the DNS response was changed and the user started downloading the infected file.
In Egypt, the technology was used to redirect users to special ads and browser scripts for mining cryptocurrencies.
Why is it dangerous?
Because you can spoof any site with anything, and an unqualified user will not even notice it. You can infect thousands of devices with keyloggers, spyware or blockers, which will download information and gain access not only to the victim’s account, but also to corporate accounts, monitor the victim’s communications. You can create and spoof sites and stole sensitive user data – card numbers, passports, phone numbers and any other sensitive information.
On the other hand, it can be a way to regulate “unwanted” traffic. That is, you can create a “white list” of resources, the transition to which will be allowed. The rest of the resources will receive a DNS response with information about the blocking. It is much easier than slowing down or shutting down any sites and requires very little resources and is also cheap to implement.
The most dangerous thing here is that this is done by a state provider, the trust in which by default is high both from users and from administrators of networks, sites, international organizations.
Is it legal?
Essentially, this is an interference with the normal functioning of the network. All such actions on the part of state bodies, regulators, special services should be regulated by legislation, where the situations in which this happens, how, why and how long it is done, should be described in detail and clearly. We are not aware of such documents.
Besides, such actions lead to a violation of the rights of citizens, which are enshrined in the Constitution and in international treaties. For example, the right to receive and spread information, the right to freedom of expression. It can also potentially be used to spy on users and their devices, i.e. interfere with privacy. This is also considered as a violation of human rights.
If we talk about attempts to introduce malicious programs – viruses, trojans, spyware – this can be qualified as computer crimes.
It should be added that the consolidation of this practice in legislation does not make it legal if constitutional rights and international obligations are violated.
What to do?
User-level solution: in this situation, it is always to use reliable VPN services that encrypt your traffic and it is not visible to the provider. You should also pay attention to the secure connection icon – it usually looks like a lock in the browser line. If it is closed, the connection is secure. If it is open, it is necessary to treat this resource with caution.
Provider-level solution: protect user traffic and allow at least unencrypted DNS queries through the VPN.
International community solution: accelerate the implementation of Internet protocols that encrypt DNS requests, making them impossible to spoof.


